Cyber Library
Here is a convenient and FREE source of information concerning Cybersecurity as it relates to government contracts.
Enjoy!
Enjoy!
Cyber Requirements

So it's pretty much "business as usual" if you have formalized risk management processes in place, are ISO 27002 certified, or have been dealing with healthcare or financial data. So this series is for the 'newbies' to the requirements being enacted to protect two broad classes of information. The first is "Government Contract Information". The second is "Controlled Unclassified Information". Knowing which type of information is being stored or processed on your system is essential since it could be BOTH.
This article introduces the basic cybersecurity requirements and sets the stage for the rest of the series.
Structured Approach
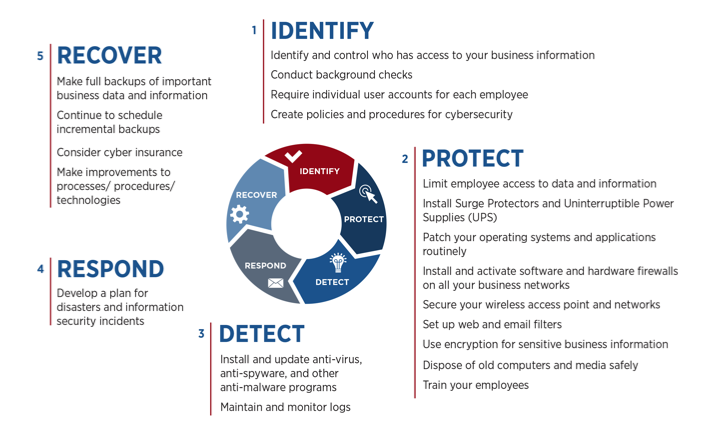
It's not rocket science mind you .. but it is a structured approach that is designed to provide consistent results. If you are familiar with basic risk management techniques such as taught in project management or financial management courses this approach will make very good sense.
Reserved
Self Assessment

The requirements are additive such that the Level 2 CMM requirements include everything from the FAR requirement and the CMMC Level 1 requirements (essentially the same requirements except verified by a third party) PLUS unique Level 2 requirements. So obviously the place to start is at lowest rung of the ladder (Level 1) and see how you are doing.
Filling the Voids

Referring back to the Structured Approach mentioned earlier you should look at each of these gaps and evaluate the risks associated with them. For example lack of an anti malware program is a big deal … likely to result in loss of data, ransoming your data, or crashing your system. Other requirements may be less serious or less likely to happen (or both) so ranking each gap in your armor is essential to prioritizing your actions.
Toward that end there are going to be some things you can do easily and cost effectively using in-house resources. But many of the steps that you have not take are not because you don't realize their importance - rather it's more a case of not having the skills or ability to implement them yourself.
Buying the latest anti malware software or instituting procedures for visitor control will very likely be among the things you can and should do and provide a lot of "bang for the Buck" in terms of cost vs. benefits. These are also things you can probably do within a day or two and will provide immediate payback.
Other steps will require some professional assistance and it's here that you'll need to do some due diligence.
Here are some things you can do TODAY at little or no cost that will help:
1. Control visitors and physical access to your equipment
2. Change your passwords … make sure you use STRONG passwords that combine lower case, UPPER CASE, numbers 182734 and symbols $%^&* and are about 12 or more characters in length.
3. Find the "update" setting for your operating system (Windows or Mac OSX) and set it to automatically update
4. Do the same with your application software … keep it up to date.
5. Update your virus or anti-malware software and allow the software to do both on demand scans (like when you open a file) and scheduled scans
6. Educate yourself concerning various cyber scams like Pfishing
7. In the words of Ronald Reagan "Trust but Verify" … A little suspicion (or caution) can be a very effective trait.
8. Back-up everything regularly both to an on-site location and to a remote location - wouldn't want fire, flood, or theft to take down your ability to operate.
Get a Pro

1. Where is the service provider and their technicians located? If you have CUI on your system you want a provider that is using US resources not offloading the work to foreign nationals.
2. What service(s) are you actually purchasing? Are you paying for monitoring services, break/fix support, hosting support etc. As in all things contractual - if it's not expressly stated (in writing) in you agreement - it doesn't exist.
3. You will tend to get what you pay for. Performing your due diligence should include reference checking
4. Sometimes you need a specialist. Cybersecurity is a pretty broad field. Some companies specialize in certain software, hardware, or systems. If you are running a Linux server you want someone who is fluent in that operating system. Linux is not Mac OSX so a Linux technician may or may not be able to do much for you if you run Apple systems.
5. If you are using hardware like a commercial firewall (or Unified Threat Management Appliance) have the reseller provide direct support for configuration and management. Also if there is an anti malware software (like endpoint security) offered by the firewall/UTM vendor consider bundling the products together.
Who's Paying for All This?

First and foremost the cybersecurity improvements are a necessary business expense and should be a tax deductible business expense.
If your company has approved indirect rates for cost reimbursement contracts the various cybersecurity expenses should be allowable as a part of your indirect rate pools and allocatable to cost reimbursement contracts.
